Whenever we talk about the basics of cybersecurity, nothing is deemed more important than passwords. The concept of passcodes was invented in the 1960s. From then on, passwords were the first and last savior of end-users and corporate data.
But with technological advancements, the old-school method of securing the financial or social accounts and databases holding heaps of sensitive data is no longer secure. It is because the hacking methodologies are also enhanced, by which the rise of cyberattacks and unauthorized access is noticeable. So, 2 factor authentication provides an extra layer of security that assists verification methods like passwords and biometrics.
Two-Step Authentication – Backing up Passwords
It’s quite obvious that the passwords are now deadly lacking a security system. The sensitive data placed over the internet needs utmost protection measures which can’t only be secured with a string of characters but can easily be guessed and information could be compromised. So, the cybersecurity measures need improvements once and for all.
The tech evolution started over the last decade. The end-users and the businesses moved one step ahead of the password, adopting high-tech cyber security methods such as the zero-trust approach. Undergoing this advancement, only the administration can gain access by providing a password. This approach was quite effective but wasn’t able to survive in this fast-moving world.
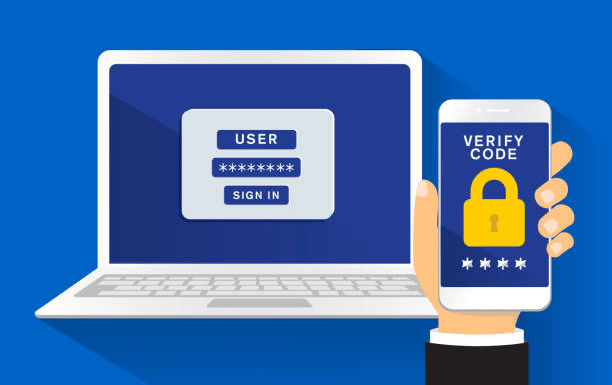
Whereas 2FA authentication uplifts the cybersecurity measure. It means that when the customers have to login into any application or website, the systems require an OTP code along with the password. These dual-checks are responsible for authenticating the request that is coming from the legitimate user.
Most of us experienced 2FA while logging on to social platforms or banking applications. While logging to any website the server sends a numeric code onto your sim or email which is to be provided in order to gain access. This means you have undergone two-factor authentication.
Two-factor authentication is a viable component for cyber protection as it is capable of neutralizing the suspicious activities associated with manipulating passwords. In any case, passwords are compromised and the imposter can’t gain access to the account with the approval of the legitimate entity. In short, security without 2fa is useless.
How does 2FA Works?
Primarily, two-factor authorization transacts in a way:
- The end-user tends to log in to the desired application of web platform by providing their credentials usually username along with the password
- Then the entered password is verified by the server, upon validation the user proceeds to the next step of verification
- The server then sends a unique 2FA security numeric code to the user’s email or on the sim number provided at the time of registration
- User by providing the code can prove his legitimacy and can get access to the account
Multiple Approaches of Two-Factor Verification
Authenticator Apps
These are smartphone applications that are used in handling the dual-factor approval procedures as basic notifications. Such applications are responsible for delivering the login approval request via the internet with the utmost protection.
Universal Two-Factor (U2F) Devices
These devices are the same as tokens. Such devices are mainly used to verify login requests. These devices are precisely designed which can be perfect for a USB slot and are also compatible with modern type-c slots. When the user wants to gain access they have to provide the credentials while UEF devices are plugged into the computer. For 2FA verification the user has to press the device physically in order to gain access.
Passcodes
These are considered the most common type of two-factor verification. Passcodes usually consist of a unique set of strings of numeric digits that are sent to the users’ registered number or email. These codes have to be entered manually so there is a risk of mishaps.
Phone Callbacks
This approach is considered as the inconvenient version of 2fa. Yet they are secure and effective but at the same time, it’s time-consuming. Moreover, distortion over the call can cause anomalies. When the user logs into the platform that has incorporated this service, they receive a call that is automatically generated by the server intended to verify the login request.
One Time Passcode(OTP)
OTP is similar to the passcodes. These are more reliable than the traditional passcodes. Rather than sending users heaps of passcodes, using this, the server generates only one passcode with a limited time. Most OTPs are valid for 5 minutes and afterward expire. This service doesn’t use any insurance channels hence considered as the safest means of 2fa
Conclusion
Two-factor authentication is another identity verification solution provided by SaaS companies. It is referred to as the value-adder to cybersecurity. 2FA has come up with loads of benefits, it secures the customer’s digital identity from breaches as well as helps them to stay compliant to the regulatory standards and guidelines. By utilizing 2FA the users’ financial accounts become unbreachable, for example in case a password gets compromised if dual authentication is enabled the intruder cant gain access unless the real user can prove the OTP. It’s the most secure way of ensuring data confidentiality.